A Tale of Burgers and Broken Security
By Love Sharma | 28 January 2026
It all started with a craving for burgers. You know the kind - the cheesy, saucy, “I-need-this-right-now” type of craving. So, like anyone in the 21st century, we did not bother calling the restaurant. We fired up a food delivery app, picked our burgers, and hit Order Now.
Everything seemed normal. The app showed us the estimated delivery time, and while we waited, wandered into the Order History section. That is when things got interesting.
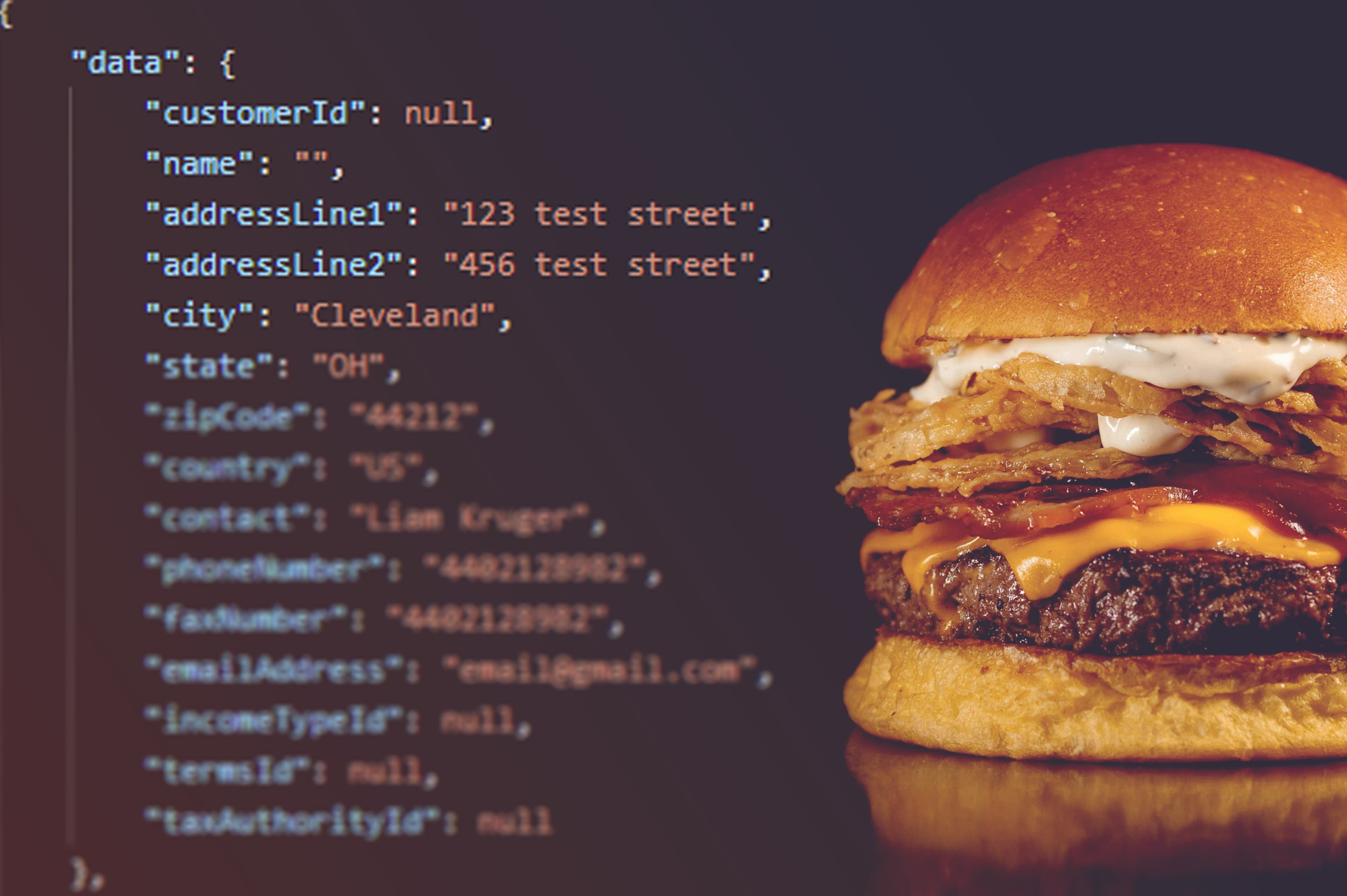
Right there, alongside our burger order, was an Order ID - a neat little number that uniquely identified our purchase. Out of curiosity, we wondered, what if we changed the number just a little?
So, we did. And just like that, the app revealed someone else’s order and their delivery address. Even the option to reorder their meal, as if it were our own order.
There were:
- No hacking tools
- No exploits
- No restricted access
Just by changing a number, access was given to the order.
What Is an IDOR Vulnerability?
What we encountered is known as an IDOR vulnerability (Insecure Direct Object Reference).
IDOR occurs when an application exposes internal object identifiers (such as order IDs, user IDs, invoice numbers, or file names) and fails to properly verify whether the logged-in user is authorised to access the request.
In simple terms:
- The app trusts the ID sent by the user
- It does not check ownership or permissions
- An unauthorised user can access or manipulate data that does not belong to them
If a user can change order_id=12345 to order_id=12346 and see another customer’s data, that’s IDOR.
Why IDOR Is So Dangerous?
IDOR vulnerabilities are particularly dangerous because they:
- Are easy to exploit
- Require no advanced technical skills
- Often exposes sensitive personal data
Depending on the application, IDOR can lead to:
- Exposure of names, addresses, phone numbers, and emails
- Access to financial records or invoices
- Account takeover
- Unauthorised actions like order cancellations or reorders
In real-world breaches, IDOR flaws have exposed millions of user records — all because access controls were missing or poorly implemented.
How Developers Can Fix IDOR Vulnerabilities?
Fixing IDOR is not about hiding IDs — it is about proper authorisation. Here are the key best practices:
- Enforce Object-Level Authorisation
Always verify that the authenticated user owns or is permitted to access the requested object. - Never Trust Client-Supplied IDs
Any ID coming from the browser, app, or API request must be validated server-side. - Use Indirect References Where Possible
Instead of sequential numeric IDs, use random or UUID-based identifiers. - Implement Role-Based Access Control (RBAC)
Ensure users can only access data allowed by their role and permissions. - Log and Monitor Access Attempts
Unexpected access patterns can help detect abuse early. - Conduct Regular Security Testing
Automated scans and manual penetration testing help uncover IDOR flaws before attackers do.
What started as a simple burger craving turned into a lesson in app security. For developers, it is a reminder that user-facing identifiers must always be validated and protected. For us, it was a reminder that sometimes, even when you are just hungry, you can stumble upon vulnerabilities hiding in plain sight.
🍔The takeaway? If your app is leaking order IDs, or any other kind of identifiers, you are serving up more than just food - you are serving
Secure Your Application Before It's Too Late
At Liverton Security, we specialise in identifying and fixing vulnerabilities before they become costly incidents. Our security assessments help organisations protect user data, maintain trust, and stay compliant.
Contact Liverton Security today to get your application assessed and secure your systems before the bad guys find the flaws.
About Liverton Security
Digital technology has greatly expanded opportunities for businesses, but has also introduced complex security threats that organisations cannot ignore. Protecting people, critical data, and entire organisations requires proactive and continuous security strategies.
As an influential and respected leader in global cybersecurity, Liverton Security specialises in helping businesses and government organisations neutralise evolving cyber threats in the digital age.
Can we help keep you cyber safe?
To explore solutions and discuss your cybersecurity needs, talk to our team at Liverton Security.
Let's Chat