Resources
Explore expert insights, case studies, news and more from Liverton Security.

Manage My Health Is Not an Outlier: Why Small Health Providers Are Being Targeted—and Why Email Is Still the Front Door
Latest News
See what’s happening at Liverton Security.

Liverton Security Implements Advanced Email Security Solution at Gill Jennings & Every LLP
Liverton Security, a leading provider of email security, announces the successful implementation of a new email filtering and threat management solution at Gill Jennings & Every LLP, one of Europe’s leading intellectual property firms.

Liverton Security Enhances Cyber Defenses for Innovation and Growth Leader Plexal
Liverton Security, a leading provider of SaaS-based cyber security solutions, is delighted to announce a new partnership with Plexal, a UK innovation and growth company driving national security progress, economic growth and social prosperity.
Case Studies & Expert Insights
Deep dive into solutions and cybersecurity topics with our experts.

One of the biggest security risks in New Zealand isn’t technology. It’s misplaced responsibility.
Many organisations assume cybersecurity is handled by their IT or network provider, but IT operations and security are not the same discipline. While firewalls, endpoint tools, and cloud controls are important, security fails when it becomes technology-led instead of risk-led. Real security requires governance, skilled people, and continual review—not just tools left to run on default settings. Without dedicated security leadership and maturity assessment, organisations can appear secure on paper while remaining exposed in practice.
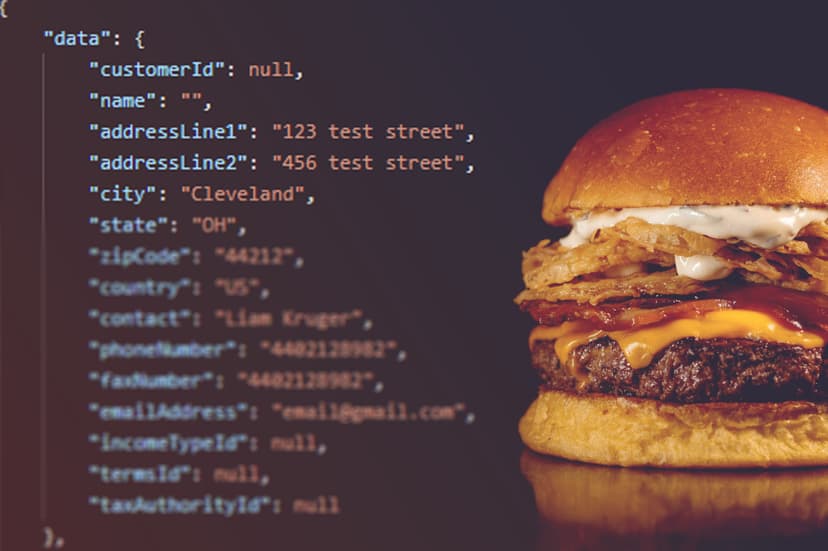
A Tale of Burgers and Broken Security
What began as a simple burger order through a food delivery app quickly exposed a serious security flaw. While checking the order history, the presence of a visible Order ID sparked curiosity. By changing this number slightly, it was possible to view another customer’s order, including their delivery address, and even reorder their meal. The incident highlights a basic but critical security failure: inadequate access controls that allowed unauthorised access to other users’ data through predictable identifiers.

Complexity of Security (Part 2)
Complexity is a sign of sophistication in security. The more tools, the more policies, the more detailed the controls, the safer we must be, right? The truth is vastly different. Complexity is the enemy of security. When security systems are too complex, they create fear, confusion, and disengagement.

Complexity of Security (Part 1)
Security doesn’t fail because people don’t care—it fails when it’s too complex. With organisations juggling dozens of security tools, confusion has become a hidden vulnerability. Cybersecurity expert, Andrew Johnston, explains how over-engineered systems and technical language drive people to bypass security, and why simplicity—not more controls—is the key to building security that actually works.

Manage My Health Is Not an Outlier: Why Small Health Providers Are Being Targeted—and Why Email Is Still the Front Door
The Manage My Health data breach wasn’t just one of New Zealand’s biggest cybersecurity incidents — it exposed a pattern affecting small and mid-sized healthcare providers nationwide. As privacy obligations race ahead of enforceable security standards, the incident points to a systemic risk and raises uncomfortable questions about how health data is really being protected.

The Human Firewall: Why Your Team is Your Best Defence Against Cyber Attacks (Part 2)
As an organisation, there is a clear need to adopt a flexible methodology that takes a holistic approach to security, with particular emphasis on business recovery.