
Uncover and address security risks in your organisation's systems.applications.
Uncover and address security risks in your organisation's systems.applications.
Strengthen your defences before they can be exploited by real-world threats.

Overview
At Liverton Security, our penetration testing services proactively identify vulnerabilities in systems—helping organisations stay resilient against modern cyber threats.
Our services go beyond identifying weaknesses. We provide clear, actionable recommendations to strengthen your system defences and reduce risk from increasingly complex and evolving security threats. This helps protect your organisation’s critical data, systems, and assets.
Every assessment is tailored to your unique business environment. We use proven methodologies and industry best practices to ensure testing is relevant, effective, and aligned with your operational priorities.
Our testing supports compliance obligations by aligning with recognised standards and regulatory frameworks, helping organisations meet both security and governance requirements.

"Security is not just firewalls and patching software. It's also about securing the everyday systems quietly running in the background — systems that attackers love to exploit."
Love Sharma, Cyber Security Analyst
Our Penetration Testing Assessments
Our penetration testing assessments cover a range of testing types designed to identify vulnerabilities across different systems, environments, and threat scenarios.
Applications and Code
Web Application Testing
We rigorously test your web applications for vulnerabilities like SQL injection, cross-site scripting (XSS), and IDOR, ensuring robust protection against cyber threats and safeguarding user data and business continuity.
Mobile Application Security
Evaluate the security of your mobile applications and APIs on iOS and Android. We pinpoint issues such as insecure storage, authentication flaws, and API endpoint vulnerabilities, providing actionable insights for secure user experiences.
Secure Code Reviews
Perform detailed reviews of your software source code to detect vulnerabilities like buffer overflows, SQL injections, and logic flaws, ensuring software security prior to deployment.
Infrastructure and Networks
Network Penetration Testing (Internal & External)
Identify vulnerabilities across your internal and external networks, simulating real-world threats to fortify your infrastructure against breaches and insider threats.
Host Configuration Security & Compliance Reviews
Conduct thorough audits of your OS, databases, web servers, and firewall configurations, ensuring compliance with NIST and CIS standards, strengthening security posture, and reducing risk.
Wireless Penetration Testing
Our testing examines your wireless networks such as Wi-Fi and Bluetooth, and ensures the proper protection is in place.
Team and Processes
Red Team Operations
Simulate sophisticated, real-world attacks including social engineering and physical security bypasses, thoroughly testing your organisation’s readiness and defensive capabilities.
Purple Team Engagements
Our collaborative Red (offensive) and Blue (defensive) teams conduct exercises that enhance your organisation’s threat detection, response, and recovery capabilities, boosting overall cybersecurity resilience.
Phishing Simulations
Evaluate employee susceptibility to phishing through realistic email and SMS simulations, significantly enhancing awareness and response capabilities to minimise attack success rates.
Cloud Environments
Cloud Security Assessments
Examine public and private cloud infrastructures (AWS, Azure, Spark (CCL), Datacom) for misconfigurations, access control flaws, and vulnerabilities, delivering tailored recommendations to protect your sensitive data and services.
Physical Environments
Physical Penetration Testing
Liverton Security offers comprehensive physical site audit that looks at the overall site’s security and how assets and staff are protected. Physical audit can include physical penetration testing that looks at the physical barriers and controls that have been implemented.
Other
Not sure which assessment you need?
Our team at Liverton Security can help review your current security practices and recommend the most appropriate testing options.
Protect your assets and reputation.
Security starts with understanding where you are. Let us map the way forward.
Let's Chat
Why Liverton Security?
Our penetration testing is delivered by Certified Ethical Hackers, including OSCP, OSWE, and OSEP professionals, with deep, real-world industry experience.
We don’t use one-size-fits-all testing. Every assessment is customised to an organisation’s systems, risk profile, and business objectives.
Our comprehensive penetration testing services support organisational compliance with recognised industry standards and frameworks, including:
- NZISM
- ISO/IEC 27001
- NIST
- and other relevant regulatory requirements
We identify and help mitigate vulnerabilities before they can be exploited—reducing the likelihood of incidents and strengthening your overall security.
Proven Expertise
Our team holds recognised industry certifications that demonstrate proven expertise in penetration testing and cyber security.














Case Studies & Insights
Explore how vulnerabilities are identified and what organisations can do to strengthen their security.

A Pentest Adventure: From Shells to Access Cards
During a network penetration test for an international client, initial access was gained by exploiting a vulnerability in a publicly exposed application. This led to command execution, a reverse shell, and ultimately full Remote Desktop Protocol (RDP) access to the system. What appeared to be a single compromised machine marked only the beginning of a much broader security story.
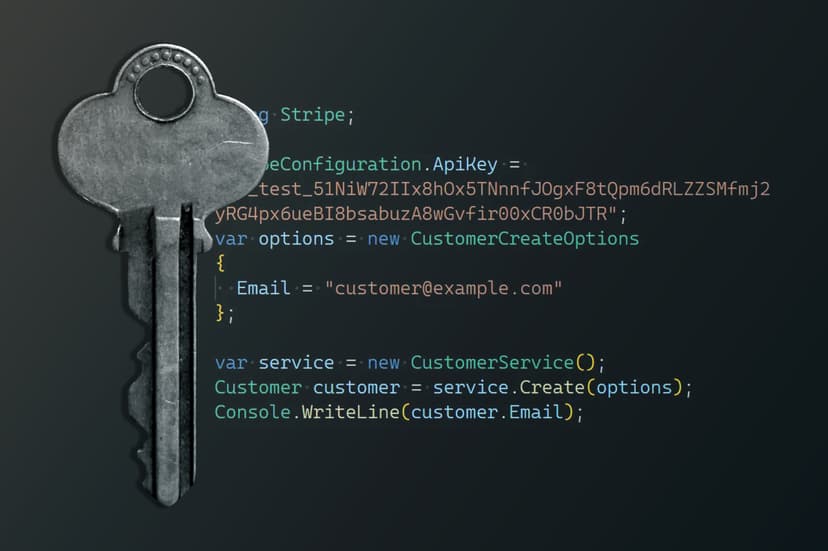
Did They Lose Their Keys? A Black Box Pentest Adventure
Old code and forgotten API keys can create serious security risks. In this black box penetration test, a valid key was discovered in an abandoned repository—proving that attackers don’t always need malware or zero-days to gain access. Learn how simple oversights can open the door to sensitive data.

Did you forget your Cat? Tom?
A penetration test uncovered an exposed Apache Tomcat server running default credentials, leading to remote command execution. Learn why forgotten systems remain a critical security risk.