Government Level Security
SmartGate is a leading edge gateway content management filter, designed to provide high grade business and enterprise email protection against growing email threats by cyber criminals, competitors and email misuse by staff.
SmartGate provides robust and government grade email security system through a low cost, scalable model – that includes threat intelligence, encryption, virus, malware and data loss prevention tools that provide high grade protection. SmartGate was originally developed for Government departments and therefore has security robustness and functionality that exceeds almost all other similar products on the market.

SEEMail
SEEMail is the New Zealand Government’s email encryption and security service, controlled by the Department of Internal Affairs (DIA)
Without SEEMail
Emails are vulnerable to attack and, when unprotected, present danger to the corporate and enterprise environment.


With SEEMail
Emails with SEEMail are protected from attack providing secure peace of mind and unharmed effective operations.
What is SEEMail?
SEEMail secures email traffic over the internet between participating New Zealand public sector organisations. The system is a gateway-to-gateway encrypted email service where the email is encrypted and decrypted by the organisation’s SEEMail server as it arrives/leaves the organisation.
SEEMail is an ‘opt-in’ service for all eligible public sector organisations. Organisations wanting to take up SEEMail do not have to complete a full procurement process as the Department of Internal Affairs (the Lead Agency) manages SEEMail on behalf of all eligible public sector organisations.

MailAdviser
MailAdviser filters email recipients, content and attachments and alerts users when a risk is detected. Protect your brand and reputation with MailAdviser.
Help prevent email data breaches by providing visibility and minimising risk.
- Seemless integration with Microsoft Outlook
- Easy to use controller interface allows flexibility
- Pop-up dialog gives key information and warnings
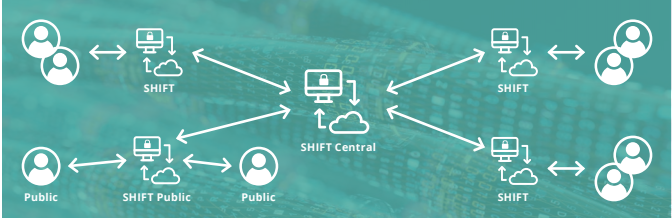
SHIFT
Move large files securely and confidentially
- Users can securely send files which are too large to send by email
- Files are signed and encrypted using PKI certificates
- Files are removed from the system once retrieved by the recipient
- Complies with the security requirements of the NZISM
- Can be used as a module of SmartGate/SEEMail or as a standalone solution
- Can be used within an organisation or between an organisation and individual public users
Domain Name System
Users of the Liverton Security Domain Name System (LDNS) use a self-service portal to manage domain and zone records.
Changes to zone records can be scheduled for a future day and time and multiple changes can be queued. The LDNS solution supports Te Reo Māori vowels with macrons.
The LDNS solution is a live-live fail-over system based in IaaS datacentres in geographically diverse centres. It is a robust and secure system.
The system uses DNSSEC (DNS Security Extensions) to strengthen authentication using digital signatures based on public/private key cryptography.
Customisation for specific requirements is available.
Liverton Security is a .nz authorised domain name registrar.
Domains
Domains move through a lifecycle of states: current/published, draft, scheduled or historic.
Two Factor Authentication
The Liverton Security DNS system uses 2FA to confirm the user’s identity.
Moderation
Domain requests move through a lifecycle of states: draft, pending approval, not published, published or declined.
Permissions
Users are assigned roles to control the functions they are able to use. Permissions are managed by the LDNS System Administrator.
Information Security Consulting
Certification and Assurance, Governance, Risk and Compliance (GRC), Penetration Testing, Information Security Strategy, IT Governance, Privacy Assessments, Identity Management Assurance, Technical Architecture Services.
Governance, Risk and Compliance (GRC)
Certification and Assurance
IT Governance Assessments
Training and Advice
Risk Assessments
Privacy and Identity Management
Privacy Assessments
Identity Management Assurance
Penetration Testing
Internal and External testing of your systems
Cyber Security Advice
Technical Architectural Services
General Cyber Security Advice
Liverton Security is in the media! Read below for an excerpt from our recently published article ⬇️
"In the fast-evolving digital landscape, cybersecurity is no longer a luxury—it’s a necessity. Yet, many organisations continue to fall into the trap of adopting generic, off-the-shelf security solutions with the assumption that what’s effective for one business will protect them all.
The reality, however, is starkly different. When it comes to cybersecurity, a “one size fits all” approach simply doesn’t work. Tailored security strategies are essential to defend against diverse threats, protect unique digital assets, and adapt to the specific needs of each organisation."
Read more in our article on tailored security on the Professional Security Magazine:
professionalsecurity.co.uk/products/cyber/tailored-security-for-threat-detection/
🌟 Meet Warren, our new GM of Development! 🌟
We’re excited to introduce Warren, who has recently joined Liverton Security in the newly created role of GM of Development. In this position, Warren will be managing our talented development team.
Warren has spent most of his adult life in Wellington and began his career in the Creative industry, bringing with him a unique perspective and a wealth of experience.
His strengths include:
💡 Leadership
🚀 Delivery
⚙️ Operations
🤝 Relationships
📊 Business acumen
We’re looking forward to the amazing things Warren will bring to the team, and we’re thrilled to have him on board! 💼
#MeetTheTeam #LivertonSecurity #Leadership #TeamSpotlight #Development
🌟 Meet Andrew (AJ) 🌟
With a rich history as a technology engineer and architect, Andrew (or AJ) has been immersed in the tech world since the days of MS-DOS and text-based interfaces. These days, he's back to his roots, focusing on compliance, audit, and security systems.
Outside of work, AJ is happily married and together they share their home with two pampered tabby cats—Bodie and Doyle—who enjoy their luxury lifestyle with a bed in every room!
A Wellington native, AJ spent his early years in South Asia and the Islands before returning to New Zealand to pursue his education. Having worked around the globe for over 20 years, he’s an avid traveller who has explored far and wide. Whether it’s cycling, climbing, rafting, snowboarding, or a fishing trip, AJ loves embracing life’s adventures!
We’re thrilled to have someone with AJ’s vast experience and passion on our team. 🌍💻
#MeetTheTeam #LivertonSecurity #TeamSpotlight #TechExpert
Richard's back in the land of the long white cloud!
After 5 successful weeks in the UK reconnecting with our resellers, partners, and potential new customers, he's ready to dive back into things here in NZ. Welcome back, Richard!
#WelcomeBack #TeamLiverton #CyberSecurity #LivertonSecurity #GlobalConnections
🎧 New Podcast Alert! 🎧
Richard Bourne, CEO of Liverton Security, recently joined the Hipther Podcast to discuss a critical topic in today’s cybersecurity landscape: Why One-Size Cybersecurity Doesn’t Work.
In this episode, Richard shares insights on the evolving nature of cyber threats, the importance of tailored security solutions, and how organisations can better protect themselves from emerging risks. 💻🔒
Hosted by Zoltan “Hawkie” Tundik, the Hipther Podcast delves into everything from deep tech to mental health, gaming, AI, and more!
👉 Listen now and hear Richard’s expert take on the cybersecurity challenges organisations face today!
🟢 Spotify: spoti.fi/3X0neZ6
🟠 Apple Podcast: apple.co/3oNnON9
🎧 More streaming platforms: hipther.com/podcast/
#CyberSecurity #Podcast #CyberRisk #TechTalk #LivertonSecurity #CyberSolutions
Secure Everything.
Protect the organization against spam, viruses, malware, emerging threats and other challenges. Safeguard employee communication and enforce security controls. Liverton Security reduces risk with targeted threat protection, data leak prevention and more.
What we can help you achieve
Take control of your business information security and discuss your requirements with one of us today.
Talk To UsContact Us Today.
Start by getting in touch with one of us. We’re ready to help.










